I will here assume you already have a remote Linux machine that you can SSH into with putty, the instructions are simple from this point on
Putty Setup
1- Basic putty settings, assuming you have already downloaded putty from chiark.greenend.org.uk, now open putty, enter the IP of the server you wish to tunnel through, and save it with a name, the steps are…
– Open putty,
– enter the IP of your remote machine
– give it a name of your choice
– save (You don’t need to save now, you will save again in a bit, but you can do it anyway)
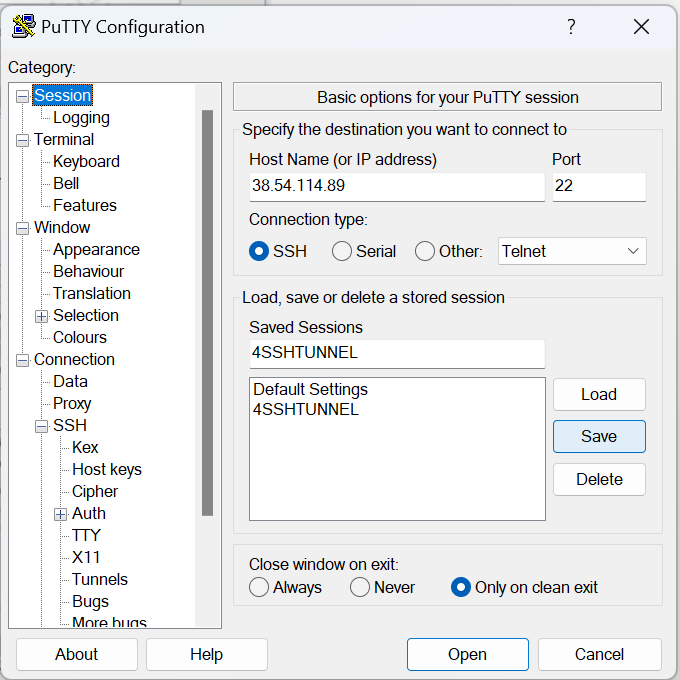
2- Go to Connection and expand it, then expand SSH, then select Tunnels, this will show a dialogue such as the below, fill in the data as follows
- A Source port between 1025-65536 (of your choice), i chose 8081 but you can chose any other in that range
- Check Dynamic and Auto, the click Add
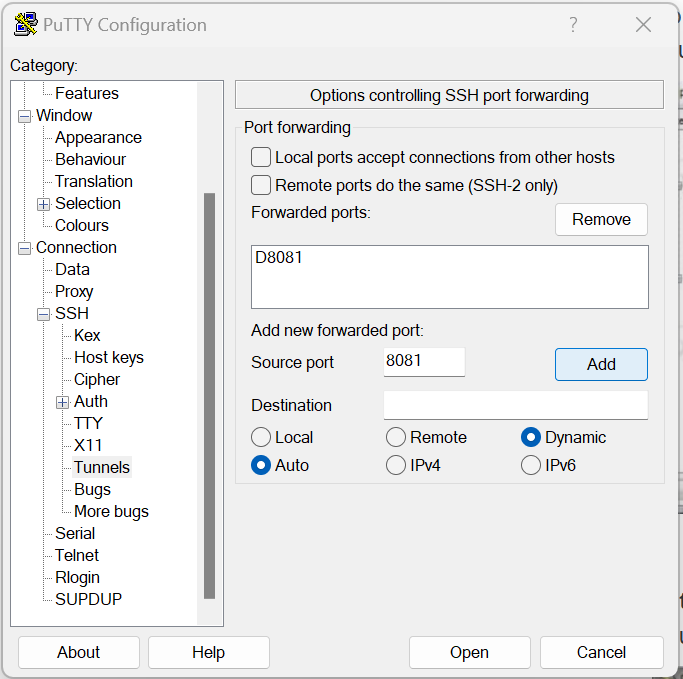
3- From the menu on the left, go back to Session, and click the save button again (So that the new tunnel settings are saved for next time)
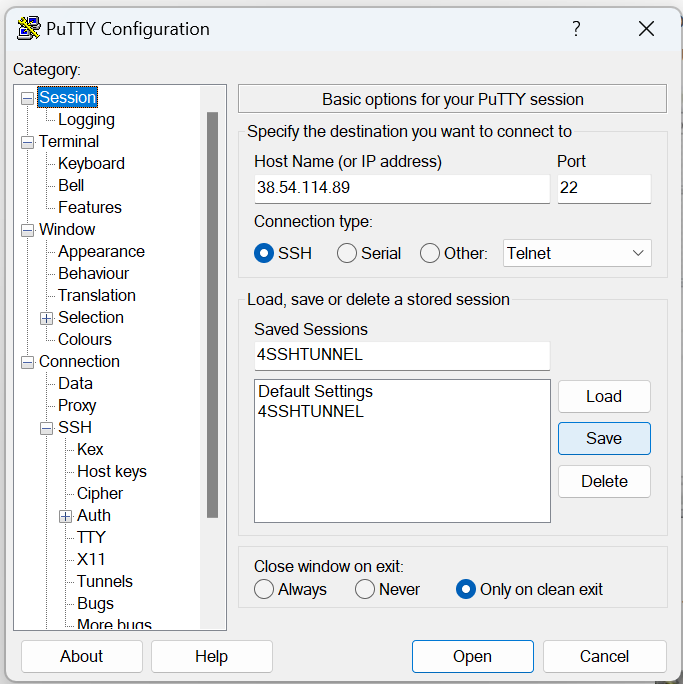
4- You are almost done, Now double click the saved session name or select it and hit open, the remote machine should now prompt you to enter a username and a password, once you enter those, you have a tunnel ready on your localhost (127.0.0.1) on port 8081, next we will setup Firefox to use that tunnel
Firefox setup
1- Go to firefox settings (Click the accordion menu to the right, and chose settings), once open, scroll down under general, until you find the Network Settings section, click the settings button in that section
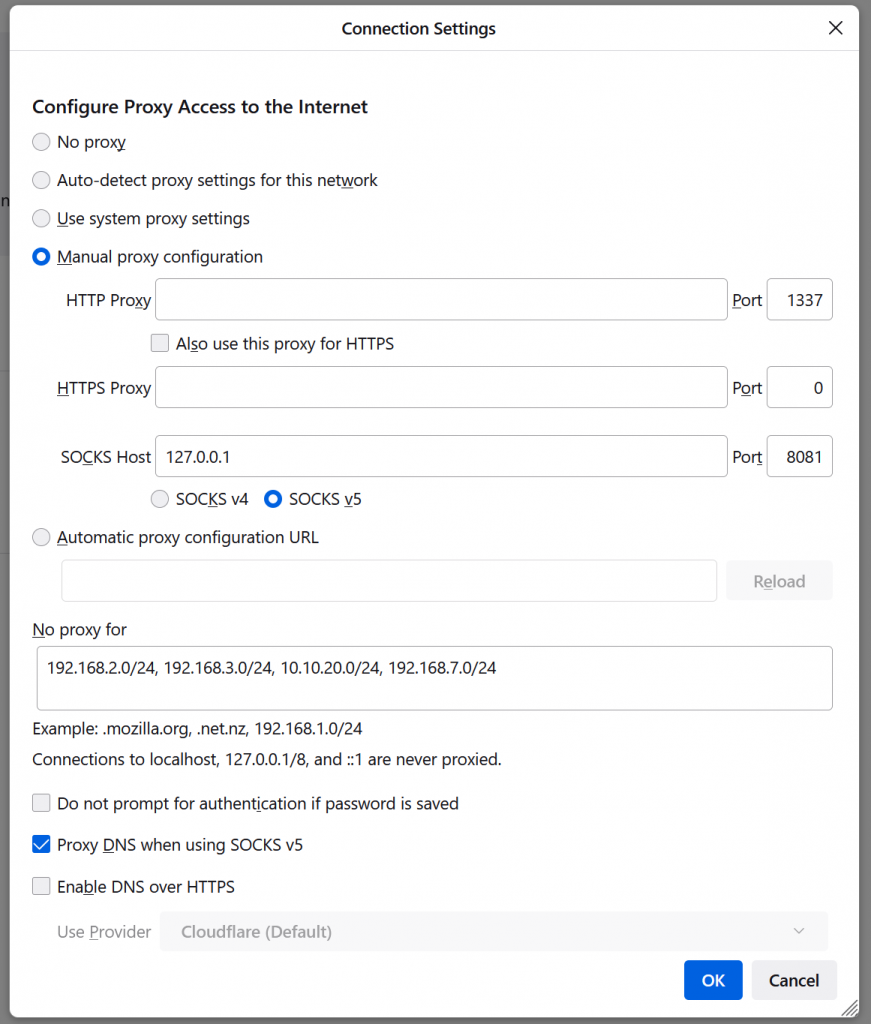
Clicking settings above will show the following popup dialogue, setup your system as follows
- Manual Proxy Configuration
- SOCKS Host enter 127.0.0.1 and in the port area of that the port we chose in putty (In my case, 8081)
- Optional – Add the IP address ranges of the IPs that you do not want to have tunneled through the remote machine
- For more privacy, and sometimes functionality (When access is blocked from abroad), make sure you tunnel your DNS queries as well (See checkbox below)
Now, to verify that you are conencted to the remote machine, google the following
what is my ip
and google should tell you what your IP address is, at this stage, it should be the same as the remote machine’s IP (Not yours)
